Phishing remains one of the most dangerous and widespread forms of cybercrime today. It is a deceptive tactic used by criminals to trick individuals or businesses into revealing sensitive information such as passwords, bank details, or credit card numbers. Phishing & Fake Payment Requests are particularly damaging because they are designed to look legitimate, often impersonating trusted companies, banks, or even government agencies.
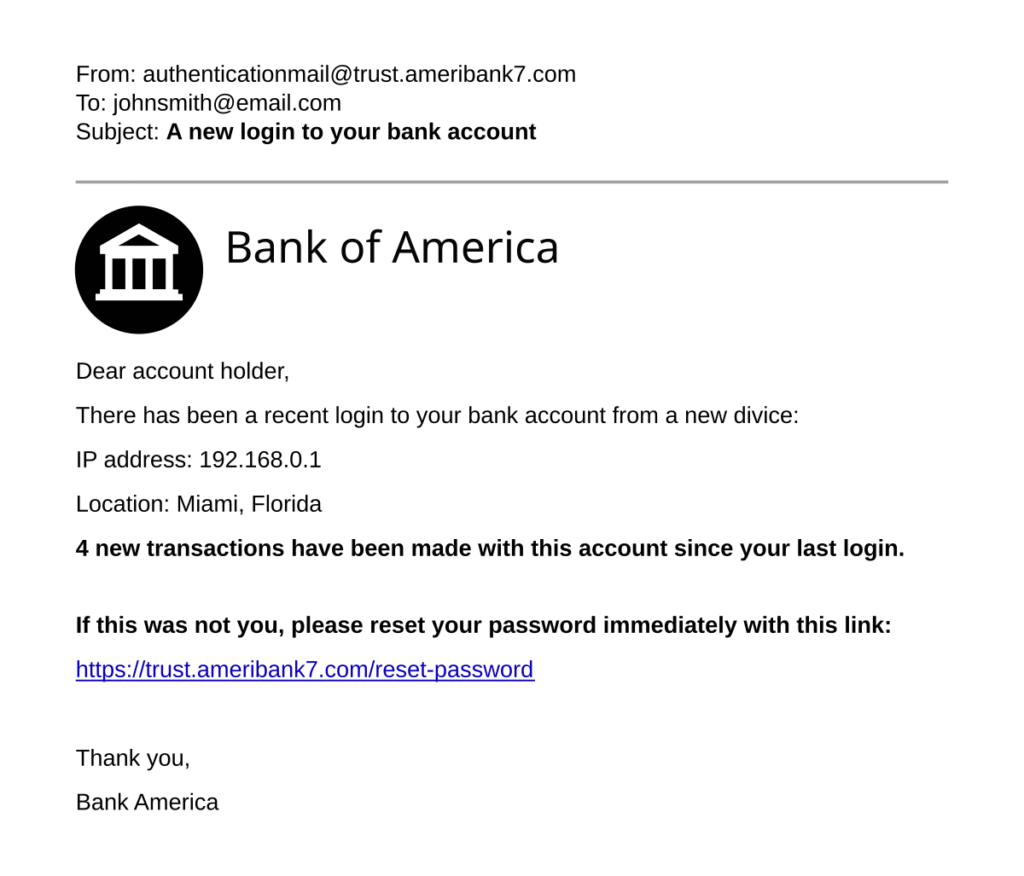
Fraudsters use carefully crafted emails, text messages, or cloned websites that look almost identical to the real thing. Victims are urged to “verify their account,” “reset a password,” or “confirm a payment.” Once the victim clicks a link or enters their details, the criminals gain direct access to personal and financial accounts. In other cases, fake invoices or payment requests are sent to businesses, pressuring them to make urgent transfers to fraudulent accounts.
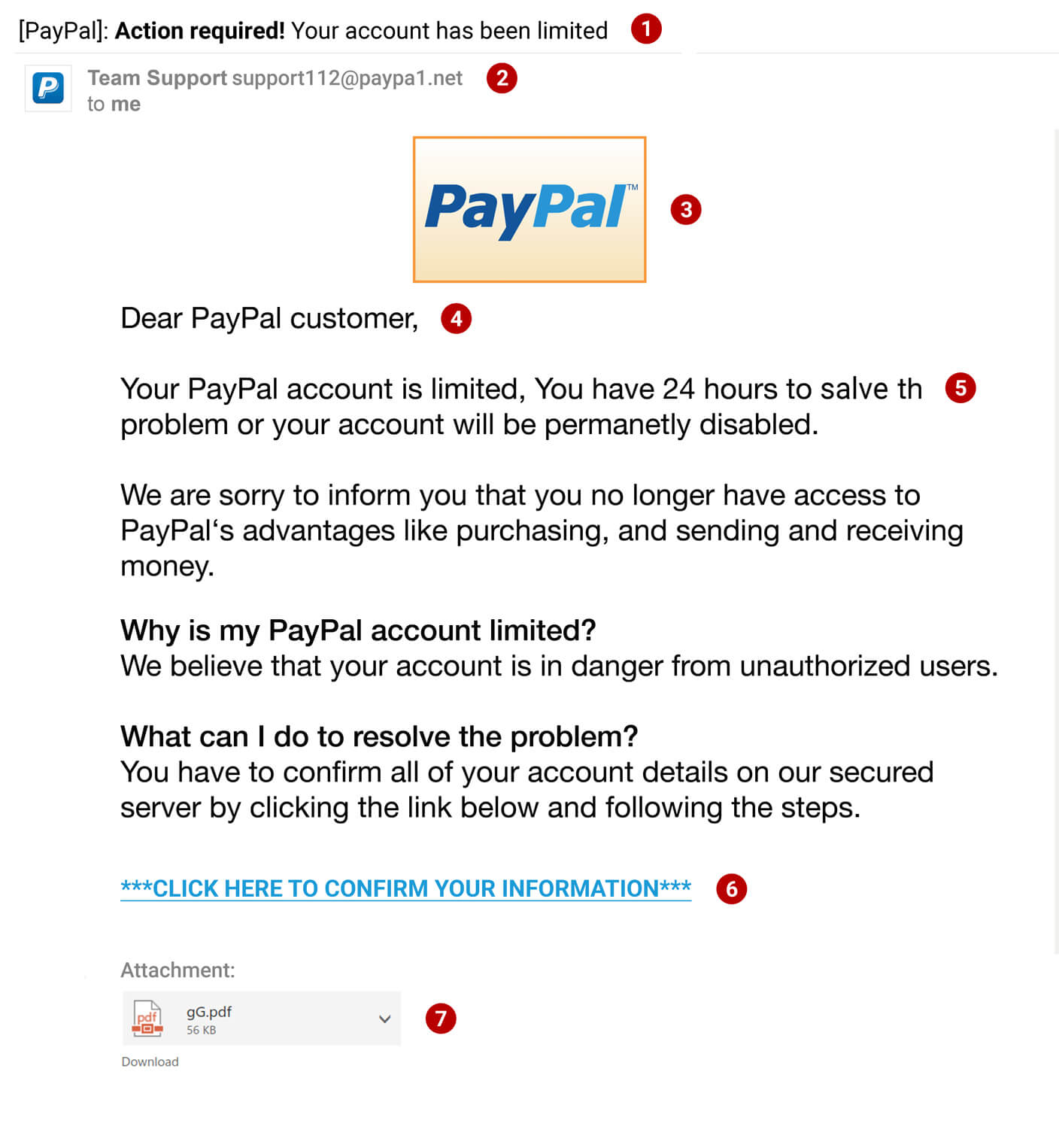
How It Works
Phishing attacks thrive on urgency and fear. Criminals design their messages to pressure victims into acting quickly, without thinking twice. For individuals, this could be an email from a “bank” claiming that their account will be frozen unless they confirm their details. For businesses, it could be a fraudulent invoice disguised as a regular supplier request.
Fake payment requests have become a serious problem for companies worldwide. Scammers often pose as vendors, clients, or even senior executives within the same company. Through tactics like “Business Email Compromise (BEC),” they send fake payment instructions that look authentic, tricking staff into transferring large sums to offshore accounts.
Sometimes, phishing isn’t just about stealing money directly. It can also involve planting malware or ransomware through links and attachments, allowing fraudsters to infiltrate an entire network. Once inside, they can steal data, lock systems, and demand ransom before restoring access.
Reports from cybersecurity watchdogs reveal that over 3 billion phishing emails are sent daily, making it one of the most common forms of online fraud. Global businesses lose billions annually to fraudulent payment requests, while individuals often lose life savings by unknowingly giving away access to their bank accounts.
Phishing isn’t limited to email. Increasingly, scammers use SMS (smishing) and voice calls (vishing) to target victims. Fake text messages about deliveries, lotteries, or tax refunds have tricked millions of people. Meanwhile, fraudsters posing as customer support agents over the phone continue to con unsuspecting victims into sharing OTPs and account credentials.
We Will Be Useful to You
At Jitte Rex Tech, we help both individuals and organizations fight back against phishing attacks and fraudulent payment schemes. Our team conducts forensic email analysis, traces IP addresses of scammers, and works with financial institutions to block fraudulent transactions. For businesses, we investigate Business Email Compromise cases and implement protective systems to prevent future attacks.
Beyond recovery, we also focus on prevention through awareness and training. We teach clients how to recognize suspicious links, identify fake invoices, and verify payment requests before acting. Cyber resilience begins with knowledge, and we make sure our clients are fully equipped to outsmart these threats.

👉 If you or your business has fallen victim to phishing or fake payment requests, contact us immediately. Acting fast can stop further damage and increase the chances of recovering your lost funds.



