Business Email Compromise (BEC) is one of the most dangerous and financially damaging online frauds targeting companies worldwide. Unlike ordinary phishing scams, BEC attacks are highly sophisticated, well-planned, and tailored to exploit trust within an organization. Criminals gain access to, or impersonate, a company’s email account to send fraudulent instructions—usually payment requests—that appear completely legitimate.
What makes BEC especially dangerous is that it often bypasses traditional security measures. The emails don’t usually contain malicious links or attachments, making them harder to detect. Instead, they rely on social engineering and the manipulation of human trust. Victims may believe they are following direct orders from their CEO, CFO, or a trusted supplier, only to later discover they have wired funds to a criminal’s account.
How It Works
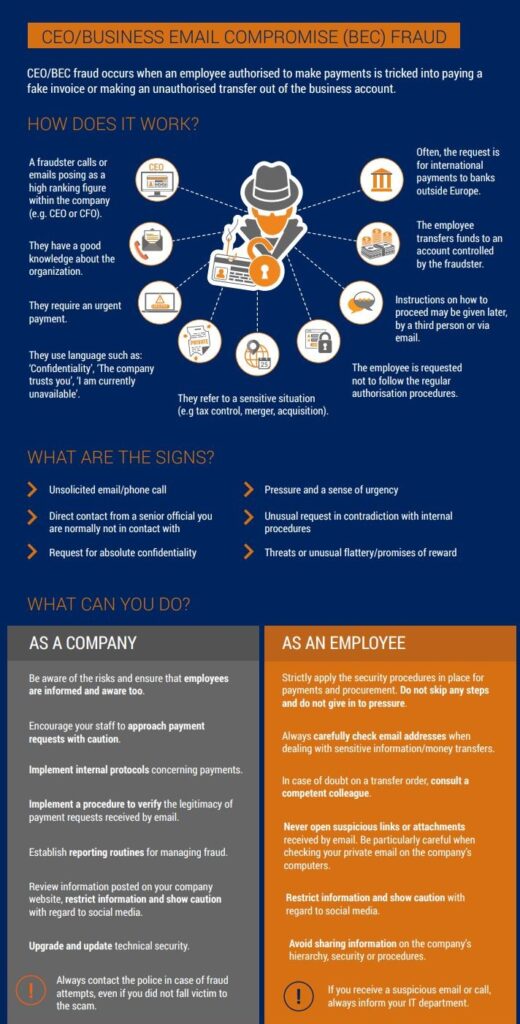
A BEC scheme often begins with criminals either hacking into a corporate email system or creating a convincing spoofed email address that looks nearly identical to a legitimate one. Once inside, they carefully monitor conversations, payment schedules, and business workflows. Timing is crucial—they wait for moments when employees are least likely to question instructions, such as during holidays or at the end of financial reporting periods.
According to the FBI’s Internet Crime Complaint Center (IC3), Business Email Compromise has caused over $50 billion in global losses between 2013 and 2023, making it one of the costliest forms of cybercrime. Unlike ransomware or phishing, BEC doesn’t require technical exploits—it succeeds because it manipulates human psychology and established business processes.
Optimization Statistics
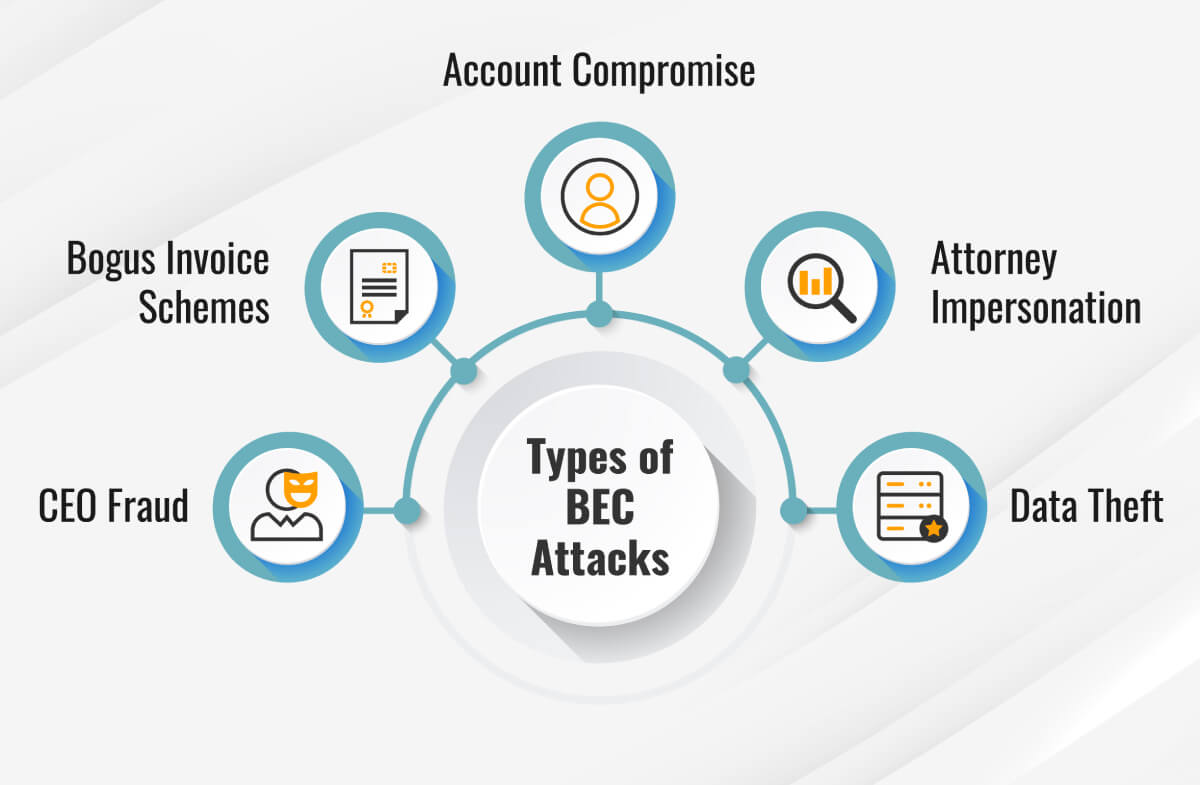
Common strategies include:
CEO Fraud: Impersonating top executives to instruct urgent wire transfers.
Vendor Invoice Scam: Sending fake invoices that mirror real suppliers.
Payroll Diversion: Tricking HR staff into redirecting employee salaries to criminal accounts.
Attorney Impersonation: Pretending to be a company’s legal representative to demand confidentiality and fast payments.
For businesses, these attacks can be devastating. Not only are large sums of money lost, but sensitive data may also be stolen. Even worse, trust between employees, clients, and partners can be permanently damaged.
In many cases, funds stolen through BEC are immediately moved across multiple international accounts, making recovery extremely difficult if not reported quickly. Small and medium-sized enterprises are particularly vulnerable because they often lack the robust cybersecurity infrastructure of larger corporations.
We Will Be Useful to You
At Jitte Rex Tech, we specialize in investigating Business Email Compromise cases and recovering stolen funds. Our team performs deep forensic analysis of compromised email accounts, traces the movement of funds across global financial networks, and works with law enforcement and banking institutions to stop fraudulent transfers.
We also help organizations build resilience by implementing multi-factor authentication, secure email gateways, and staff awareness training. Preventing BEC is not only about technology—it is about teaching employees how to spot unusual requests, verify transactions, and slow down when pressured by urgency.

👉 If your business has been targeted by Business Email Compromise, contact us immediately. The faster you act, the higher the chance of recovering lost funds and protecting your organization from future attacks.



